How to Prevent Liquidity Vampire Attacks in DeFi?
If you are a DeFi project owner or planning to become one you probably have heard about recent vampire attacks in DeFi. We are sure you do not want your project to be attacked by one of those vampires, so in this article we are going through recent attacks and tell you how to prevent liquidity vampire attacks.
The main idea of DeFi and DEXs in general is built around constant liquidity flow. So, there always should be a high demand of buying and selling some assets within certain protocols.
In case liquidity is coming out of the protocol or there is no trade within a pool, it becomes dead and useless. Therefore, all existing DEXs protocols become liquidity dependent.
What exactly is a vampire attack in defi?
The core concept behind vampire attacks in defi is, surprisingly, quite simple. The main idea lies in creating the same (or approximately) the same protocol, but empowering it with a more profitable and attractive incentive mechanism.
Read more about incentive mechanisms of AMM in our article How AMM works: Technology Basics
For instance, the development of a protocol similar to Uniswap, will not cause many difficulties as long as Uniswap smart contracts code is open source or visible on Etherscan. So, in order to create such DEX, the one should just fork the repository with code of the protocol, provide his new specific changes and deploy contracts on Ethereum.
Introducing a very strong incentive mechanism for liquidity providers is the basics of liquidity vampire attacks. Then, it is just a matter of time when to expect a huge wave of liquidity to your new-born “forky” project. Such actions are called migration mining.
Read Also: AMM Types & Differentiations Examples Use Cases.
Migration mining
Migration mining, simply MM, is a way of getting liquidity to a liquidity depending protocol out of other protocol or protocols.
The two main conditions for migration mining protocols to be successful are a long lock-up period, and the migration process itself. So, the process looks as follows:
- the user see the opportunity of getting more incentives for his liquidity
- takes his liquidity out of the protocol A
- supply this liquidity to protocol B
- (important!) lock-up this liquidity for a certain period of time
- get a reward in protocol B tokens (an incent) for liquidity providing.
The lock-up period is crucial in terms of migration mining and vampire attacks in defi because it ensures long-term lockdown of liquidity within protocol B. This helps to hold it until the competitor (first protocol A) will not be defeated.
Read Also: How to Avoid Impermanent Loss and Front-running Problem in DeFi.
Those malicious actions were named vampire attacks because project B literally sucks the liquidity from project A. This term was firstly introduced by Martin Krung in Cryptonative.
Simple liquidity vampire attacks
A simple vampire attack in Defi relies on the fack, that the “fork protocol” B has its own token, while protocol A does not have it. In this case, the performance of such attacks on liquidity is quite simple.
Project A does not possess any reward tokens and pay out just a small share of a transaction fee to liquidity providers. Due to very low incentive possibilities in project A, LPs will look for other opportunities to get in.
Therefore, LPs see attractive opportunities and migrate their liquidity to Protocol B. In exchange, they receive protocol B tokens accordingly. As a result, project A starts to gradually lose liquidity and the trade volume becomes low. This is the way how Uniswap recently has suffered from such kind of attack.
More about Uniswap attack in the next parts of this article.
Advanced liquidity vampire attacks
In the advanced model of liquidity vampire attack, both sides – Protocol A and Protocol B – should have a token.
In advance, the malicious project B starts to lend as much A protocol tokens as it can. Then it starts to sell A tokens while actively buying its own B tokens on the market and establishing a higher price for token B by this.
The price for token A is getting lower and LPs start to think of migrating their liquidity to other protocols. At this time, vampire protocol B offers very attractive terms for LPs, in case of migration and long liquidity lock-up. Therefore, LPs start to migrate from Protocol A to protocol B.
The liquidity is being “sucked away” out of protocol A and its crashing while protocol B can celebrate the successful attack finish.
Sushiswap attack on Uniswap
The summer attack on Uniswap has become one of the most discussing topics of this year in crypto. The attack was made by protocol called Sushiswap and, as we said before, is the example of a simple liquidity vampire attack.
The attack
As long as Uniswap had not had its own token then, the main incentive for LPs was the reward in SUSHI token they recieve in case of getting in. The reward was quite generous and established as 1000 SUSHI per one Ether block (so every 15 sec!) distributed in exchange for Uniswap LP tokens (confirmations of token shares in Uniswap) being provided into pools of SuchiSwap. Provisions were distributed across many different pools like in the case of YAM attack.
? Wow, @UniswapProtocol 24hr trading volume is higher than @coinbase for the first time ever
— Hayden Adams ? (@haydenzadams) August 30, 2020
? Uniswap: $426M
? Coinbase: $348M
Hard to express with how crazy this is. pic.twitter.com/48o0xRkiUo
The liquidity pool tokens started to flow as a flash to “forky” Sushiswap. Just within a few days (on 4th September) the TVL (total value locked) reached around $1.8B locked in Uniswap itself while $1.6B of Uniswap LP tokens were held in Sushiswap. It is worth noting that at the beginning such an attack on Uniswap pursued users to supply liquidity to Uniswap, so it considerably grew its power on the Defi market then.
After enough pool tokens came to the vampire Sushiswap, the next step was to carry out an actual migration. It can be done by exchanging Uniswap LP tokens for the initial assets provided to Uniswap at the first place.
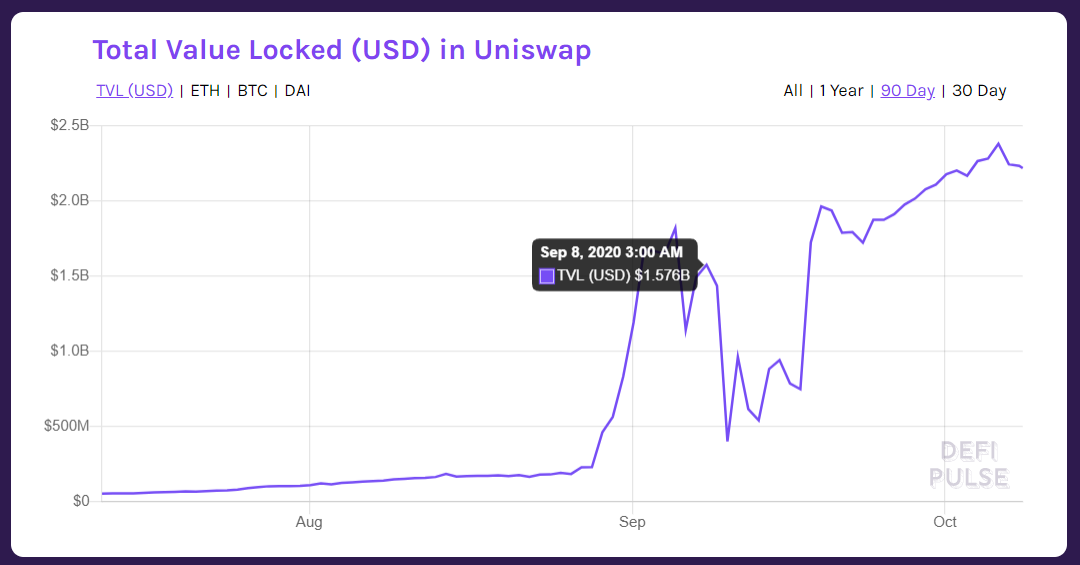
The attack was performed on the 9th of September and drastically influenced the TVL of Uniswap.
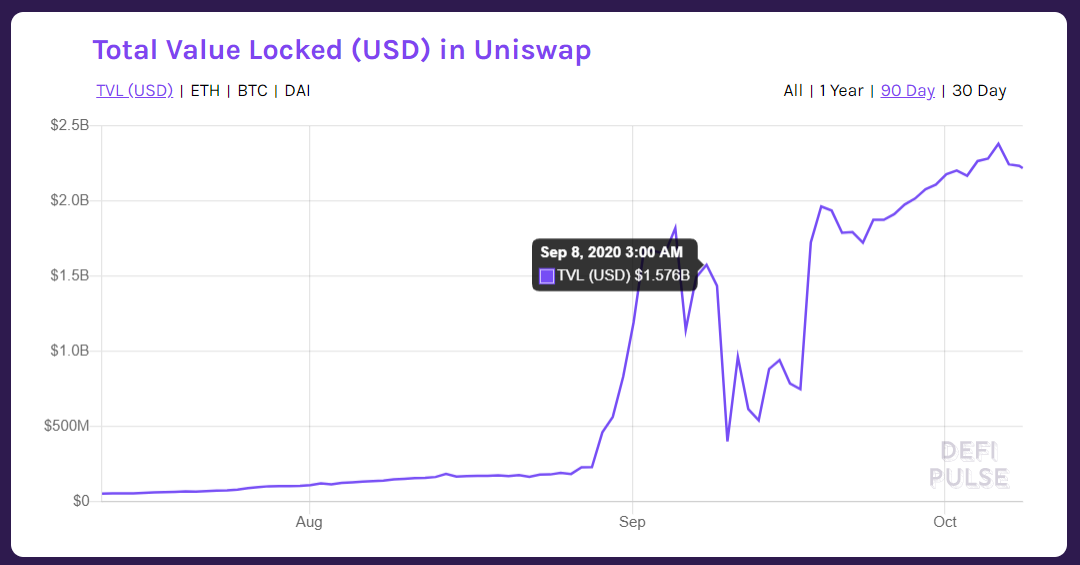
The attack was performed on the 9th of September and drastically influenced the TVL of Uniswap.
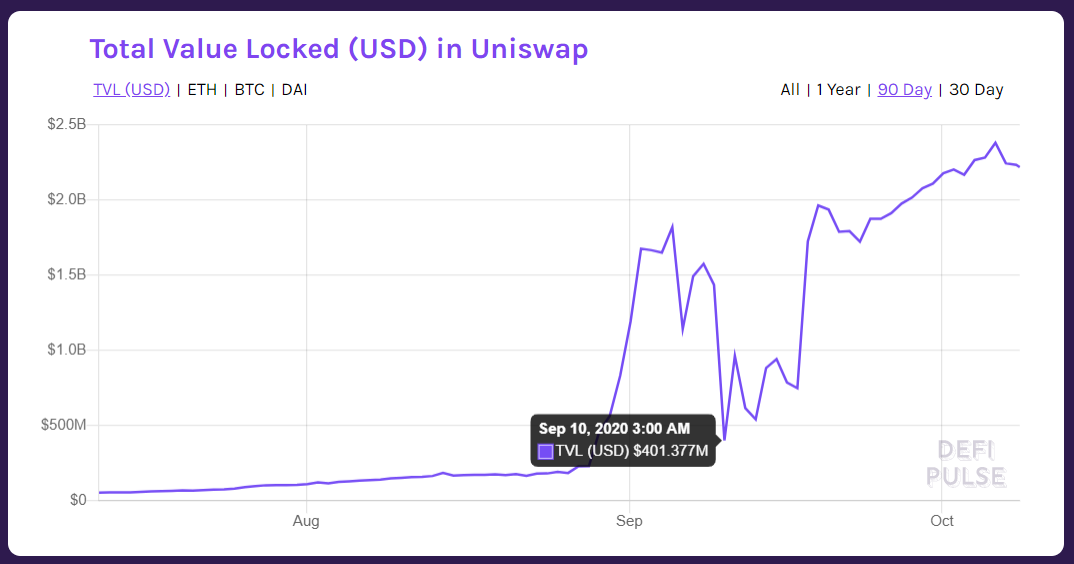
The amount has changed to $401.377M within one day (but in practice it took seconds).
Read more of Sushiswap vampire attack here.
Contact Blaize and build your own DeFi application with the team of experienced DeFi developers!
The result
Right after the Uniswap attack, it was hard to predict any further actions. Yet, there was surely a question whether users will stay after the “high reward” program is finished or come back to its initial roots.
One of the crucial actions was the emission and distribution of Uniswap’s own governance token UNI. After the attack, the protocol owners decided to distribute 300 UNI tokens to every user, which was a very generous offer, as long as it cost around $3.5 per single token then. So, multiple users just got $1500 out of nothing. It resulted in huge token price fluctuations and led to a phenomenal trading volume of UNI token.
As we can see from the graphs above, the TVL of Uniswap started to grow continuously already at the end of September. Moreover, it went even higher while beat its record point on October 6th, and reached over 2.3 billion dollars of TVL.
Swerve Protocol
The Curve.fi experienced a similar after the malicious vampire attack of Swerve protocol. Launched at the beginning of September it seemed to take over Curve users very quickly. It got more than $400 million of Curve TVL within just a couple of days. This became another “big news” in the media all around.
Yet, it turns out that being a copy-fork is not enough. The protocol governance and its, surprisingly, UI bug played against Swerve.
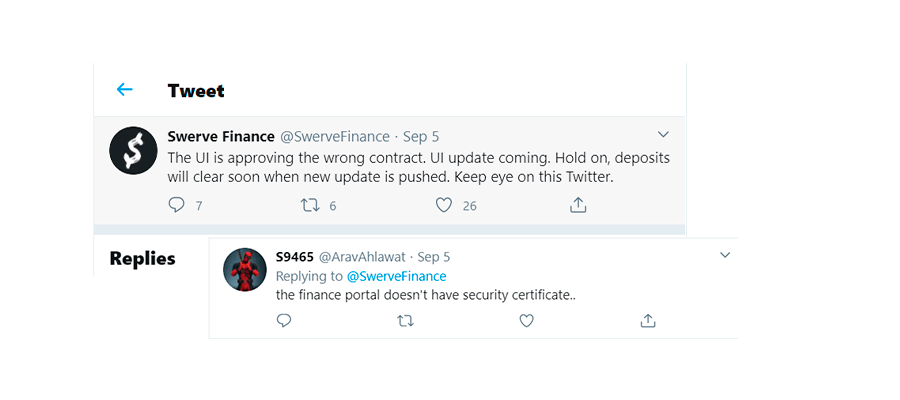
The huge buzz around the vampire Swerve has shut down quickly and users returned to Curve, similarly as we experienced in the case of Uniswap attack. Moreover, Curve protocol volume increased not even twice in comparison to the previous month according to Crypto Rank Platform.
Therefore, as the experience shows, the incentivization works just for a short-time game for now. So, liquidity vampire attacks are not sustainable yet, mainly because the community stays loyal to initial projects.
But it might not be the same for smaller or younger players on the DeFi market.
How to prevent liquidity vampire attacks on your protocol?
Attacks of this kind are quite predictable in case of such big players as Uniswap or Curve, yet not limited to those. As long as the protocol is open-sourced, the protocol developers might be aware of such vampire forks.
1. Create DAO
The experience of Uniswap attack has shown that the lack of governance token (and DAO powered by that token) might be a serious disadvantage of the protocol. The token issuing and thoughtful tokenomics were the main reasons for Sushiswap success on the market.
Therefore, it is better to consider adding this task to your “main matters” list. In Blaize, we are experts in smart contract and token emission development, so empowering your DeFi protocol will not be an issue.
See how we rebuild the initial token in snglsDAO Use Case
In addition, consider creating your own “liquidity reservation” offer. Think of alternative or additional incentive mechanisms for users so that they do not want to live your protocol.
2. Provide full coverage of unit tests
One of the reasons for such a deleterious attack on liquidity might be the confidence of providing a better product on the market. Often, there might be serious code bugs, if trying to test in a hurry or deploy your project without any test at all.
We recommend to cover your smart contracts and dApp functionality with 100% of unit tests in order to omit any future troubles. Remember, that your DeFi project will deal with a huge number of real money, so you surely do not want to lock a couple of millions of dollars on the contract forever. Furthermore, after successful test coverage, the smart contract security audit is also required.
3. Community
As simple as it is, listen to your dedicated community more often. The protocol users always share some thoughts on how to enhance their UI experience. Try to catch up with the community and do not miss those recommendations. It will surely help you to meet your unique participants’ requirements.
Find more tips and recommendations on How to Develop a Successful DeFi application in this article!
Conclusion
Recent attacks have opened a true Pandora’s box of the DeFi. The huge effort behind creating and developing such forky attacks on liquidity as Swerve and Shushiswap did, has shown that the power of Curve and Uniswap grow exponentially and gather more and more attention.
On the other hand, malicious actions contributed to protocols’ growth and enhancement. Uniswap has recently issued its governance token and Curve is working on fixing old smart contract vulnerabilities.
We have underestimated the importance of LPs’ incentive processes. Well, liquidity vampire attacks brought such valuable questions to attention. Now we can surely say, its relevance has increased the same as the protocol governance issue in terms of DEX environment.
Make sure your DeFi protocol is well tested while smart contracts work is carefully audited by Blaize!





