How to Boost Smart Contract Security and Mitigate Risks in DeFi
In the world of cryptocurrencies and decentralized finance, security has always been one of the top priorities. And it’s no wonder – everyone wants to be sure that their personal data, as well as funds, won’t be stolen.
Unfortunately, the industry has faced more hack attacks recently, and only a few projects are ready to move with the times and boost the security of their smart contracts and protocols.
That’s why today, we’d like to bring this issue up and discuss the ways protocols can be compromised, and how to enhance defi security.
Here at Blaize, we’ve been dealing with developing and auditing smart contracts for over five years now. By this time, we have deployed 400+ smart contracts and conducted 120+ audits. During our audits, we’ve detected more than 250 high-risk vulnerabilities, thus saving over $100M from potential hacks for such projects as 1inch, PEAKDEFI, and Aurora.
Moreover, our team has helped develop and secure the DeHive platform and all the financial instruments. Today, we’ll share more details on this case, too. So off we go!
DeFi market security overview
The DeFi industry has never been secure. Sad but true. Over the last eleven years, the market has experienced 364 different security incidents that have led to $14.6B stolen from various protocols and platforms. What is more, one-third of these hacks and breaches were reported in 2022. So improving smart contract security must be our top priority now.
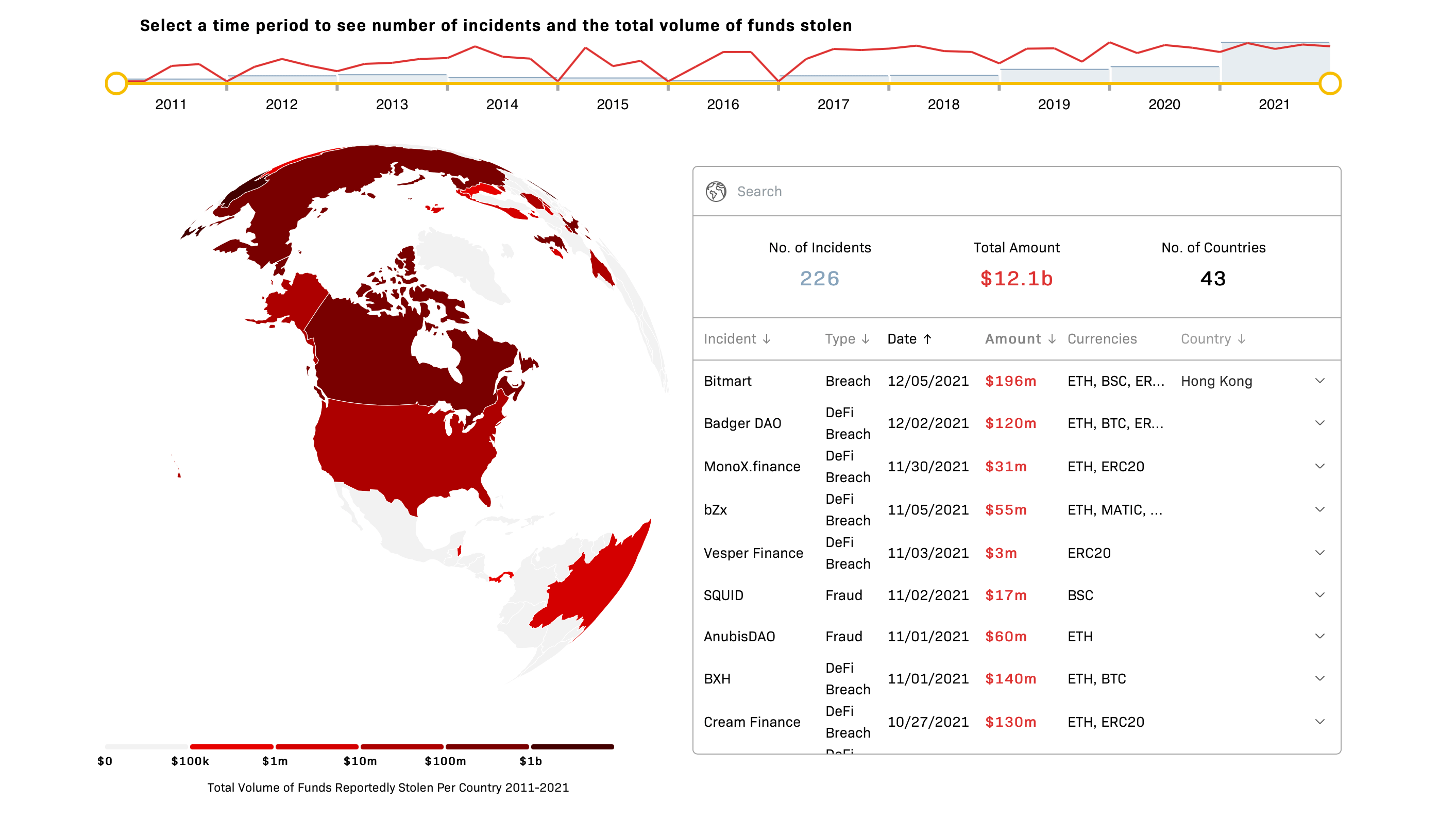
Overall, from January 2011 till July 2022, there have been 167 DeFi hacks, 123 security attacks, and 74 fraudulent schemes. You might have heard of some of them, including the recent Ronin Network incident that resulted in a $624M loss or the biggest Ponzi scheme in history that led to a $2.9B loss.
Learn more about DeFi hacks and how to prevent them in our article: DEFI SECURITY AUDIT: HOW TO PREVENT YOUR DEFI PROJECT FROM HACKING?
Of course, some of these 364 incidents might have been prevented or the losses could have been minimized if protocol owners were more concerned about their project security. Yet, sometimes, the breaches occur due to mere neglect or carelessness.
That’s why we offer you to look through various DeFi security risks, hoping that they will come in handy when writing secure smart contracts or protecting your protocol. Additionally, we highly recommend considering professional enterprise blockchain development services to ensure the highest level of security and reliability for your project.
Main security risks in DeFi
There are dozens of ways the protocol security can be jeopardized – from tiny bugs in the smart contract code to more severe problems. Let’s talk about the most common risks and types of attacks in DeFi.
- Code vulnerability. Simple coding mistakes can lead to pretty serious losses if a team hasn’t checked smart contracts before deployment or neglected security audits.
- Smart contract logic. Occasionally, some inexperienced developers or auditors might miss the lack of logic in the whole smart contract and its underlying processes. For this reason, we believe that the best practices for smart contract security must include a profound knowledge of business processes and traditional financial instruments.
- Access control. If smart contract access control is implemented inefficiently or not at all, hackers could gain privileged access to a smart contract and exploit value to their advantage.
- Liquidity pool estimates. If a project team hasn’t calculated the value of tokens in the liquidity pool correctly, bad actors might perform flash loan attacks leveraging smart contract vulnerabilities for their benefit.
- Compromised private keys. The DeFi security risks connected with stolen or leaked private keys emerge due to poor key generation practices with an insufficient source of randomness. Besides, they might occur due to a loss or theft of the seed phrase used to remember a private key.
- Frontrunning attacks. Hackers might look for the transaction they could compromise by leveraging the Miner Extractable Value (MEV) and including it in the ledger prior to the original one, thus, getting profit.
- Ponzi schemes and rug pulls. Unfortunately, some DeFi security risks emerge not from some external threats but from protocol owners and project teams. It’s a shame that such cases still take place since they decrease DeFi credibility and impede global adoption.
- Flash loan attacks. One of the most common security risks in DeFi in the last couple of years is flash loan attacks. Flash loans are a form of uncollateralized loans that can let bad actors borrow governance tokens and manipulate the protocol to their advantage. Such attacks are pretty popular these days since they are comparatively low-risk and low-cost, while bringing high rewards.
As you can see, the DeFi industry is far from being a bank vault. Yet, there are several things protocol owners can do to protect their products and users. So let us share our ultimate smart contract security tips.
READ 9 MOST COMMON SMART CONTRACT VULNERABILITIES FOUND BY BLAIZE
Best Practices To Protect DeFi Protocol
At Blaize.Security, we deal with DeFi security on a daily basis, so we’ve decided to share several recommendations and best practices for smart contracts security. Previously, we posted a longer article on this topic, so we’ll just add the key points below, but you can check out the full piece for more details and examples.
- Perform a full unit test to detect the functionality problem in separate parts of the contract and eliminate them at the very beginning.
- Contact several auditors to conduct a smart contract security audit. This will help you detect uneven and unexpected vulnerabilities of smart contracts before project deployment and, therefore, prevent DeFi hacking.
- Ensure code uniqueness. Copy-pasting code from other protocols might speed up development but lead to future exploits due to incompatible pieces of code that don’t go together.
- Take care of contracts’ access protection. To prevent unnecessary private key access or protect your DeFi protocol in case of key loss, consider using a separate multisig contract or the multisig logic within your protocol.
- Hire an experienced team of DeFi developers with accurate knowledge of DeFi project vulnerabilities and specifications.
- Turn to your protocol community to help with bugs and mistakes. Launching a bug bounty campaign will allow you to improve the user experience within the protocol and successfully defend it from potential hacks.
- Ensure you keep full and up-to-date documentation for your code base.
All of the tips and hints mentioned above are true for securing Ethereum smart contracts, as well as working with any other chain. Make sure to follow common sense and critical thinking and work with a team of real experts you can trust.
Best Smart Contract Security Tools You Should Know About
When improving smart contract security, you might want to focus on the acute issues and use the best-performing tools. Here’s a brief list of the security instruments the Blaize team can recommend to ensure high security of our customer’s protocols:
- Mythril – software for detecting bugs that shows which part of the code is responsible for each input execution. The tool is perfect for Hedera, Ethereum, Quorum, Tron, and other EVM-compatible chains.
- Slither – Python-based software that allows analyzing Solidy code with low false positives.
- Scribble – runtime verification tool that translates high-level specifications into Solidity code. It’s a great tool for securing Ethereum smart contracts.
- Echidna – a Haskell program designed for fuzzing/property-based testing.
- Vertigo – a mutation testing framework designed to work specifically for smart contracts.
Find more details about each of these tools in our article: HOW TO DO A SMART CONTRACT AUDIT OF YOUR PROJECT, AND WHY IT IS IMPORTANT
How Blaize.Security Helps Protect DeHive Protocol
Our team was creating the DeHive platform and all the financial tools that lay within it with the end-user in mind. That’s why security has always been and remains our top priority.
One of our team’s goals was writing secure smart contracts for the DeHive protocol. That’s why, as our highly skilled developers finished working on smart contract development, we conducted an internal smart contract audit to make sure that it is as secure as possible.
Besides, we’ve contacted two other leading auditing teams, Hacken and Zokyo, to conduct our smart contract security audits. This way, we could double-check the protocol and make sure that it is safe for users and smart contracts can be deployed.
You might check the final reports on these smart contract audits via these links: Hacken, Zokyo.
On top of that, we’ve created a crypto index technology that follows best practices for smart contracts security and allows us to have no real access to users’ funds. Let us tell you a bit more about that.
If you haven’t heard of DeHive before, it is an asset portfolio management platform that allows users to benefit from highly secure crypto indexes.
DeHive Clusters are yield-generating crypto indexes that unite the best-performing assets into one basket. Every index is carefully composed by DeHive experts to reflect a particular market segment, bring maximum profit, and provide users with a secure way of investing in different protocols.
Such a solution aims to facilitate traders’ lives and enable making profit in just one click, simultaneously mitigating market fluctuations due to portfolio diversification. Besides, the team has rejected AMM technology and substituted it with advanced oracles, which made the protocol even more secure.
As we’ve already mentioned before, DeHive does not have any real access to users’ funds. All deposited money is stored either on the Cluster contract, which works as a security vault, or in the original farming protocol. This protocol’s strategies are optimized regularly, so it ensures higher security of all DeHive instruments.
With all these tools and strategies, the team is providing DeHive users with a safe space to get maximum profit in DeFi and stay confident in their tomorrows.
If you’d like to learn more about DeHive and its financial products, check out these resources:
- Crypto Indexes, and How They Are Better Than Regular Cryptocurrencies
- DeHive Impulse: Automatic Compound Interest for DeFi
- DeHive 2021-2022 Roadmap
- DeHive Whitepaper
Blaize Experience
During more than 5 years of our work in the blockchain industry, Blaize experts have figured out how to improve the security of smart contracts. We have deployed over 400 contracts and audited 120 more. Our specialists have worked with the leading projects in the field, including Aurora, 1inch, PEAKDEFI, Celo, Everstake, Solana, and so much more. You can check all case studies on our website.
With all this experience, we have seen all common smart contract vulnerabilities and found ways to eliminate them. Thus, we’ve detected over 250 high-risk vulnerabilities in the audited contracts and helped the protocols save over $100M from hacking.
The Final Word
In the ever-changing world of DeFi, protocol security is the key to project success, and we are proud to say that we’ve helped many businesses achieve it.
We hope that more projects will prioritize security in the future and take proper care of their smart contracts, protocols, and most importantly, users. We’d really love to build a highly secure DeFi future together, and it’d be fantastic if you joined us on this journey.
FAQ
How to improve the security of smart contracts?
The best way to ensure high security of your protocol is to high security of your protocol is to hire reputable blockchain auditing companies and conduct at least two smart contract audits. This way, you’ll be able to check your contracts for bugs and other vulnerabilities and get extensive recommendations on their elimination.
Besides, you should always follow best industry practices and use up-to-date tools for improving smart contract security.
What are best practices for smart contracts security?
Best practices for smart contract security include the following:
- Perform a full unit test.
- Conduct smart contract security audits.
- Ensure code uniqueness.
- Use multisig logic to prevent unnecessary private key access.
- Hire experienced DeFi developers.
- Launch a bug bounty to get help with bugs and mistakes from your protocol community.
- Keep full and up-to-date documentation.
Can smart contracts be hacked?
Yes. There are many known vulnerabilities that can be used by malefactors to attack the protocol and steal data and funds. That’s why it is crucial to ensure high security of the protocol and smart contracts, follow industry best practices, and conduct regular audits.
What tools can I use to secure smart contracts?
Some of the most efficient tools for ensuring high smart contract security include Mythril, Slither, Scribble, Echidna and Vertigo.





